Authentication
Zephyr provides multiple options in which users can be authenticated when they log into the system. This is referred to as Primary Authentication.
Primary Authentication are:
Internal
LDAP
Atlassian Crowd
WebService
Single Sign-on
Secondary Authentication: If LDAP/Crowd/Webservice is being used for primary authentication and certain temporary/migrant/external users that are not in those systems need access to Zephyr, the secondary authentication option can be turned on to allow that.
Please note that this process is only for authentication and not for synchronizing user information with these systems.
Primary Authentication
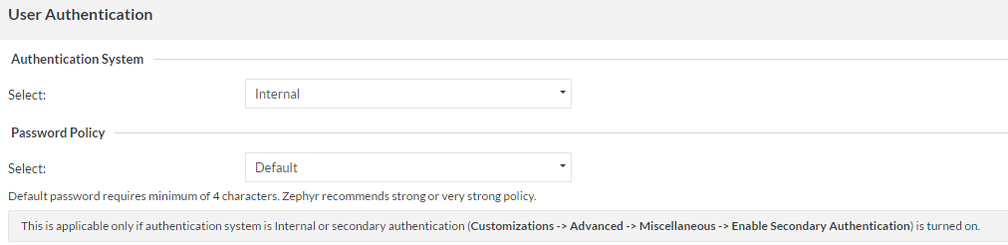
1. Internal
Administrators can leave the selection at 'Internal' to use the native Zephyr authentication system. The user ID and passwords that are stored in the User Setup section are used to authenticate users.
- This is the default option.
- Users can reset their own passwords by clicking on the 'Profile' link in the top right corner of their interface.
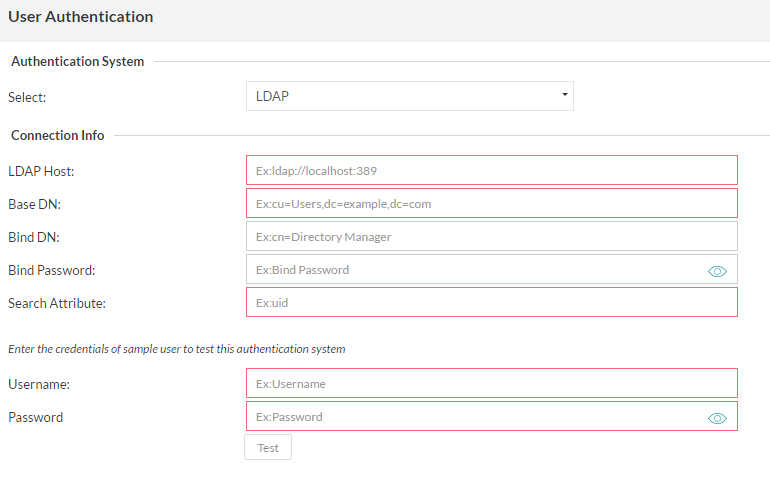
2. LDAP
If your organization is using an LDAP server for authentication, the Zephyr Server can be setup to authenticate users using LDAP.
Below the 'Connection Info' section there will be a place to test the connections and LDAP credentials used. This is useful for a quick check to see if everything is working. The username and password here can be a user in your directory that you wish to log on the Zephyr system with. Once the information is correct you can click the 'Test' button and if everything goes correctly, you should see a 'Validation Successful!' popup. Otherwise, start troubleshooting the setup.
LDAP Setup Details and Example
The LDAP authentication system in Zephyr allows an Administrator user the advantage of using a LDAP system to authenticate Zephyr users outside of Zephyr itself. Below are detailed descriptions of the fields in the LDAP authentication setup.
LDAP Host [REQUIRED]: The IP address of your LDAP instance (default port 389). Currently does not support HTTPS.
- Example 1: http://192.168.105.138
- Example 2: ldap://192.168.105.138
- Example 3: ldap://sec.ad.mainsystem.com:389
BASE DN [REQUIRED]: Folder and Domain where the users will be that need authenticating.
- Example 1: CN=users, DC=ad, DC=mainsystem, DC=com
- Example 2: OU=users, DC=ad, DC=mainsystem, DC=com
BIND DN: Admin user, Folder, and Domain that will be used to search the other folders. This user/Directory Manager MUST have the ability to look through the domain for the users that need authenticating.
- Example : CN=Admin, CN=users, DC=mainsystem, DC=com
- PASSWORD: Password for the BIND DN Admin/Directory Manager user. The show password option will just allow the user to see the password input.
- SEARCH ATTRIBUTE [REQUIRED]: The attribute that the BIND DN user will use to find the users it is searching for. This will likely be "samaccountname" on AD systems.
- Example: samAccountName
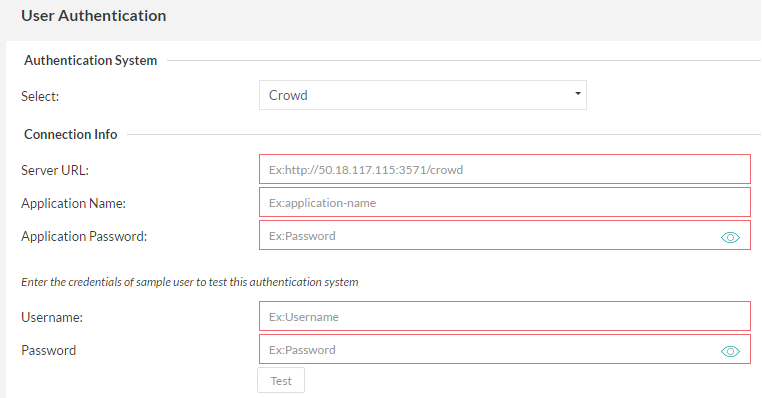
3. Crowd
If your organization is using a Crowd server for authentication, the Zephyr Server can be setup to authenticate with Crowd before allowing users to log into the system.
After entering the relevant 'Connection Info', the authentication can be tested by entering the username and password of a user and clicking on the 'Test' button. This provides feedback on whether the authentication system was reachable and if the authentication was successful or a failure.
4. WebService
If your organization is using a different authentication system, then you could write a WebService that the Zephyr Server can call to authenticate against before allowing users to log into the system.
After entering the relevant 'Connection Info', the authentication can be tested by entering the username and password of a user and clicking on the 'Test' button. This provides feedback on whether the authentication system was reachable and if the authentication was successful or a failure.
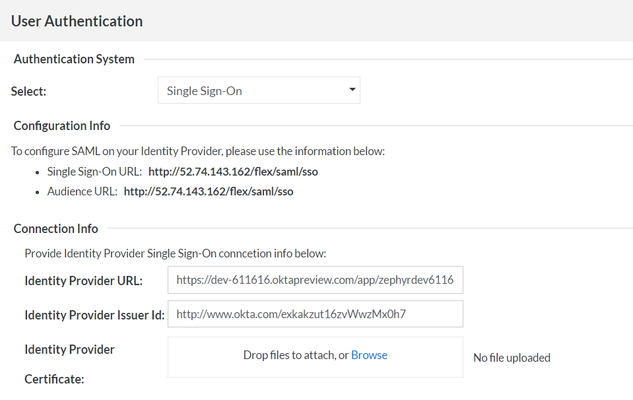
5. Single Sign-On (SSO)
If your organization is using a Single Sign-On (SSO) for authentication, the Zephyr Server can be setup to authenticate with it before allowing users to log into the system.
Secondary Authentication
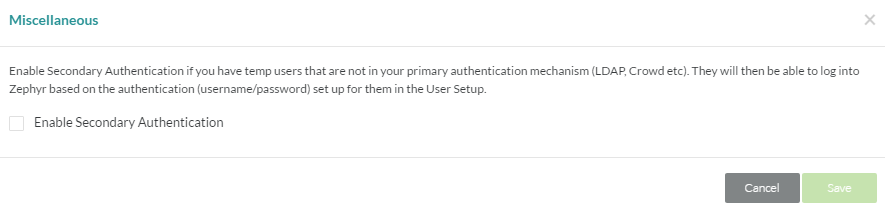
If LDAP/Crowd/Webservice is being used for primary authentication and certain temporary/migrant/external users are not in those systems and need access to Zephyr, the secondary authentication option can be turned on to allow that.
Those users are then authenticated based on the user ID/password that is set up for them in the User Setup section. Turn on this secondary authentication option as follows:
- As a Zephyr Administrator, open the Administration section
- Click on the 'Customizations' tab.
- Click on the 'Miscellaneous' button in the Advanced section.
- Check off the 'Enable Secondary Authentication' option a then click the 'Save' button.