Okta LDAP Configuration
About
LDAP (Lightweight Directory Access Protocol) is an application protocol used to access authentication data of users or user groups stored on LDAP directory servers during user authentication. Zephyr supports user authentication via LDAP.
Okta is a cloud identity management system used to access both cloud and on-premises applications.
If your organization uses Okta for LDAP authentication, you can configure Zephyr Enterprise to allow Okta users to access it (for information on how to configure Okta single sign-on, see SSO Setup with Okta in Zephyr).
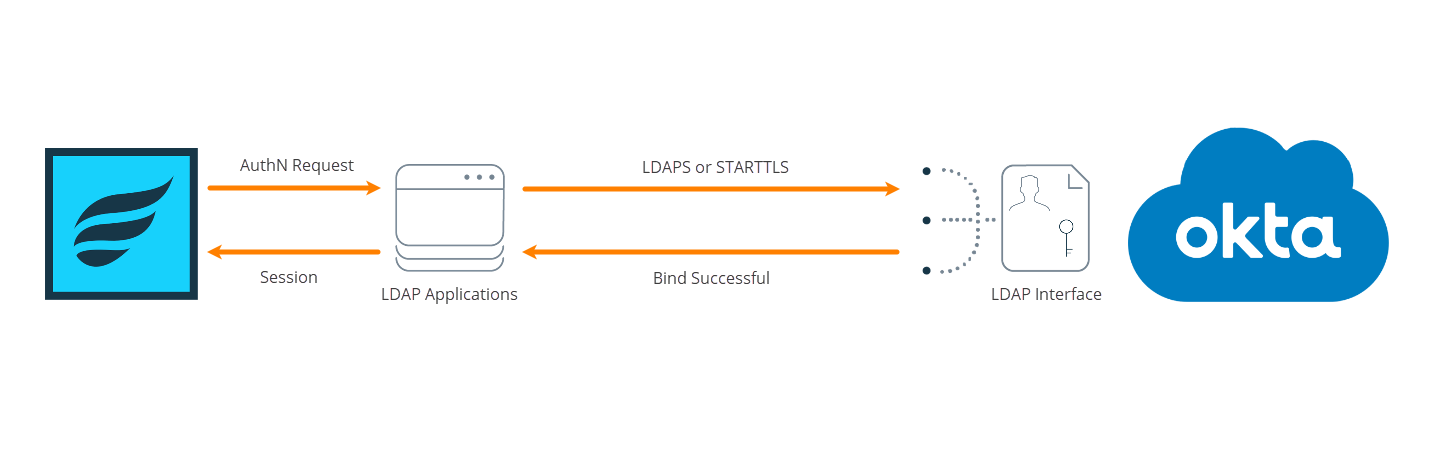
The image below demonstrates the authentication procedure:
Prerequisites
You need to have an Okta account.
Users must exist in your LDAP directory.
Configure Zephyr
To configure Zephyr to work with Okta:
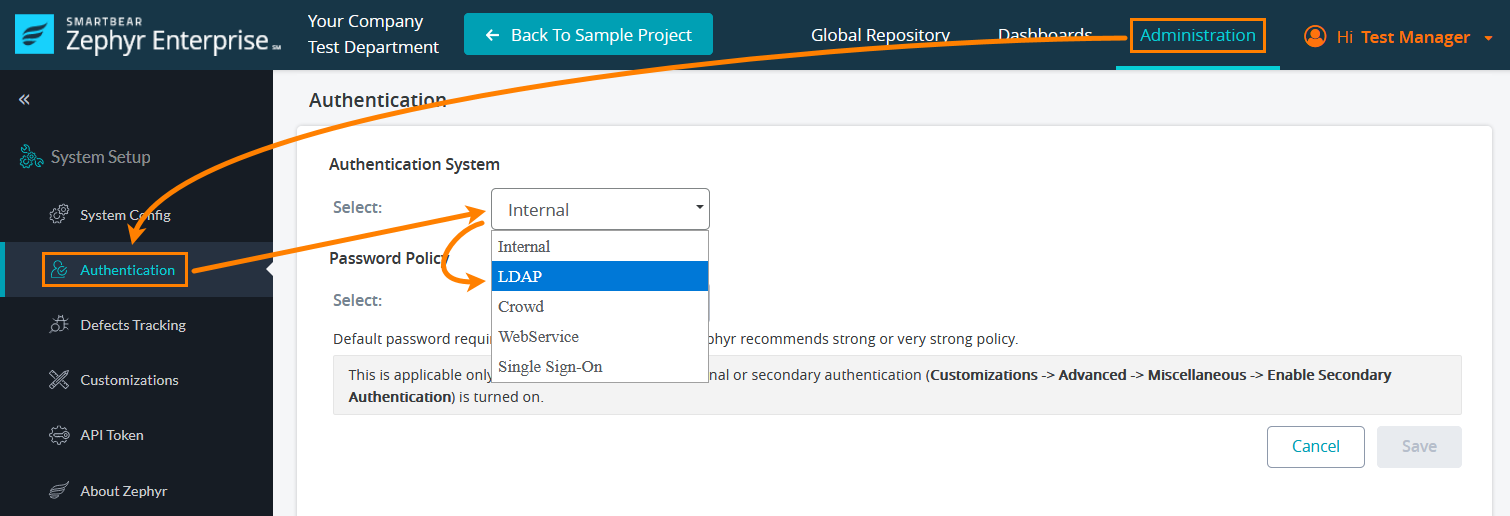
1. Log in to Zephyr as an administrator.
2. Go to Administration > Authentication and select LDAP from the Authentication System drop-down menu:
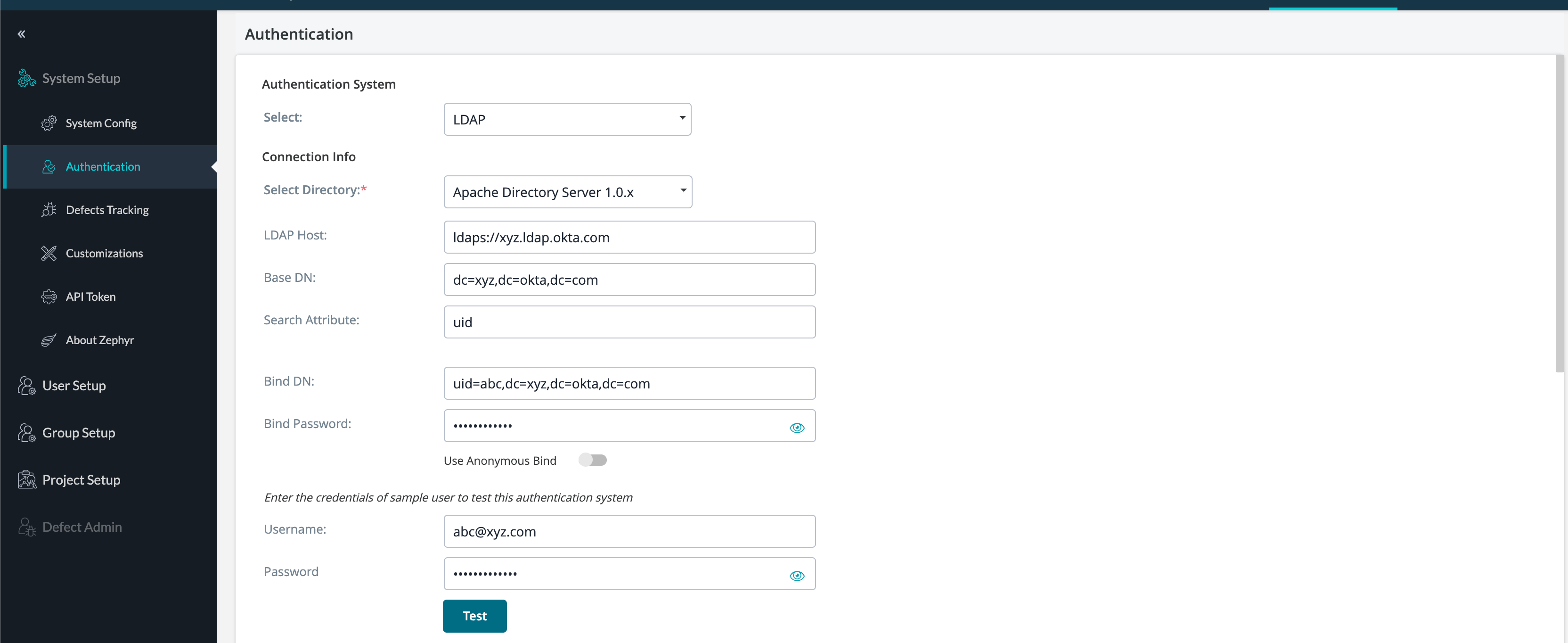
3. Fill in the fields. The settings you specify on this screen vary depending on the application you use. In our example, we use the following connection info:
Setting | Value | Example |
|---|---|---|
Select Directory | Apache Directory Server 1.0.x | |
LDAP Host | The host name of your LDAP server you access through Okta.
where | ldaps://xyz.ldap.okta.com |
Base DN | The root location where the application will start searching for users and groups.
where | dc=xyz,dc=okta,dc=com |
Search Attribute |
The search attribute to use when loading the username. | uid |
Bind DN | The distinguished name used to connect to the LDAP server.
where Note: Must be an admin, but can be a Read-Only admin. | uid=abc,dc=xyz,dc=okta,dc=com |
Bind Password | The the admin user’s password used to connect to the LDAP server. | password |
Username | The username of the sample user used to test authentication. | abc@xyz.com |
Password | The password of the sample user used to test authentication. | password |
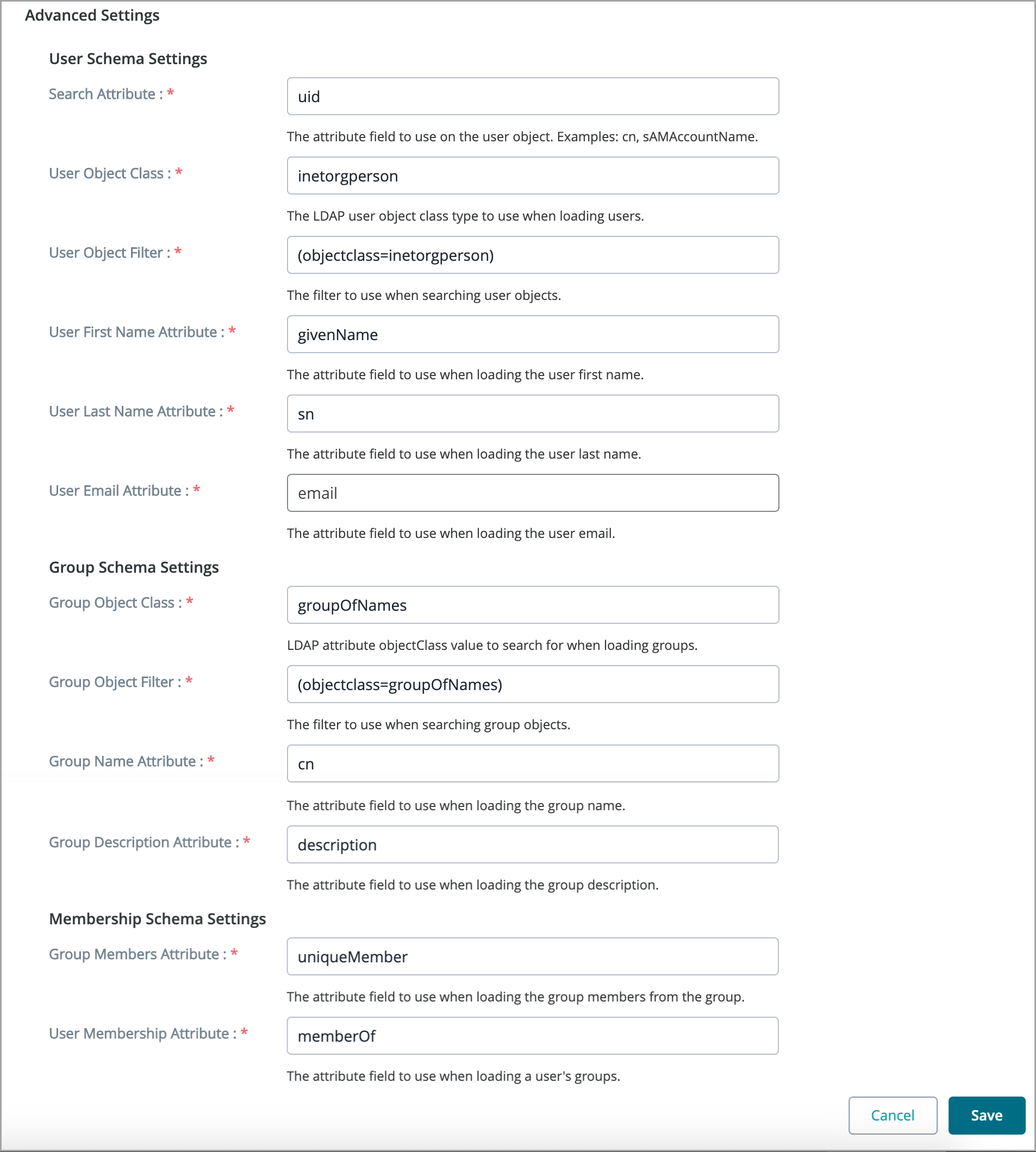
When you select Apache Directory Server 1.0.x in the Select Directory field, Zephyr will show advanced settings. All the fields of these settings are populated automatically:
memberOf is not an indexed value. Using memberOf will result in slow search time.
4. Click Save to apply the changes.
Now you can authenticate user access to Zephyr by using Okta.